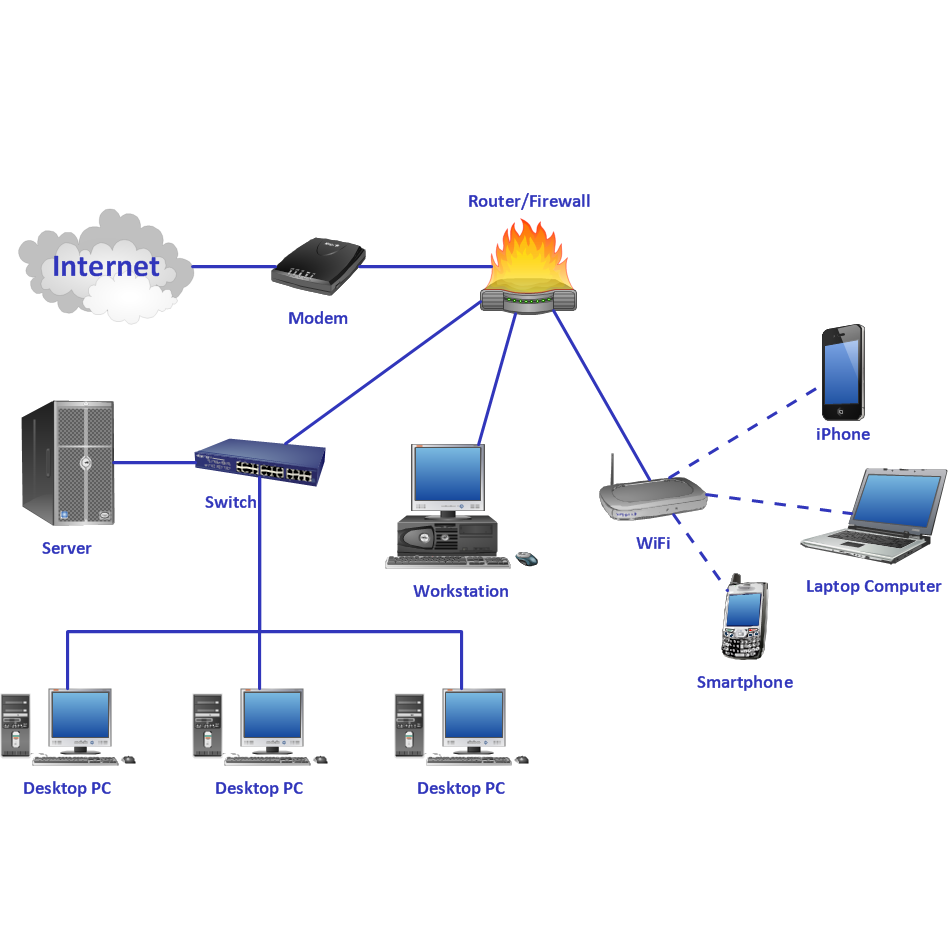
Introduction to ARP in Computer Networks
Address Resolution Protocol (ARP) is critical in facilitating communication within computer networks. As a foundational element, ARP provides a necessary bridge between two distinct network identifiers: IP addresses and MAC addresses. IP addresses, or Internet Protocol addresses, allow for the logical identification of devices on a network, while MAC addresses, or Media Access Control addresses, serve as unique hardware identifiers assigned to network interface cards. The role of ARP is to map these IP addresses to their corresponding MAC addresses, ensuring that data packets find their way to the right physical device on a LAN (Local Area Network).
Understanding ARP is fundamental for network engineers and IT professionals. Its smooth operation underpins a network’s ability to function efficiently, allowing devices to communicate seamlessly. When a device on a network wants to interact with another, ARP steps in to translate the target device’s IP address into a MAC address, thus enabling the initiating device to form a communication channel at the data link layer. This process is crucial for data exchange within the same network.
ARP operates silently yet effectively in the background, maintaining communication flow without the need for constant user awareness or intervention. It aligns with the concept of abstraction in computer networks, where complex operations are masked to simplify user interaction. In practical terms, ARP’s role is hidden from the average user’s experience, but it is invaluable in maintaining the integrity and functionality of network communication.
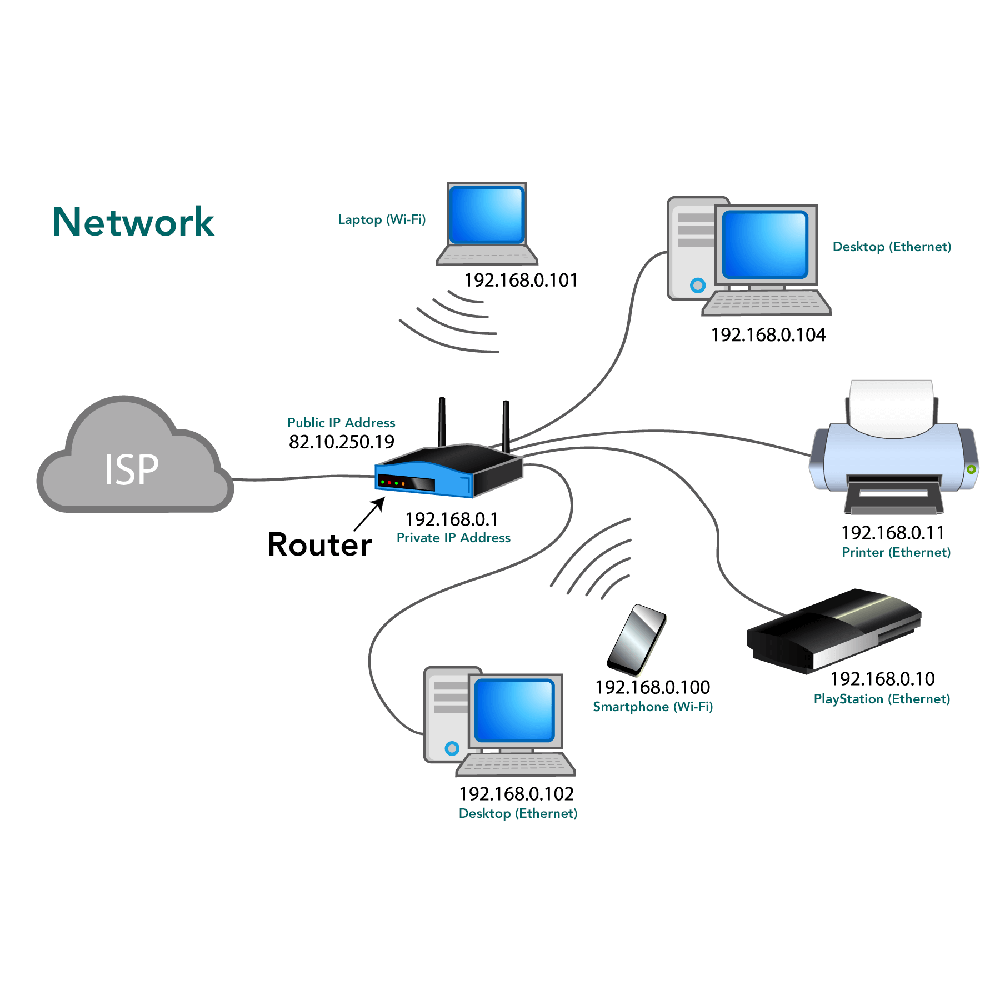
The Importance of ARP for Network Device Communication
The Address Resolution Protocol (ARP) is vital for network device communication. This protocol is the glue that connects an IP address with a MAC address, which is necessary for network interactions. Here’s how ARP underpins network device communication:
- Bridges Logical and Physical Identifiers: ARP bridges the logical world of IP addresses with the physical world of MAC addresses. Without this protocol, devices wouldn’t be able to communicate, as the network wouldn’t know which physical device corresponds to which IP address.
- Facilitates Data Packet Delivery: By translating IP addresses to MAC addresses, ARP ensures data packets are delivered to the correct device. It’s like a postman who needs to know the exact house to deliver a letter to, not just the street name.
- Supports Network Efficiency: Without ARP, devices would have to broadcast messages to every device on the network to find the recipient, drastically slowing down network speed and efficiency.
- Critical for Local Area Networks: ARP is especially vital in LANs, where many devices often interact on the same network segment. It keeps local traffic local, without the need to pass through an external router.
- Enables Internet Connectivity: For a device to access the internet, it must communicate with its gateway router. ARP finds the MAC address of the gateway for the device, which allows for successful internet connectivity.
In conclusion, ARP is an indispensable part of network communication that maintains a fast, secure, and reliable network environment. It is a behind-the-scenes player that has a major impact on daily network operations.
How ARP Works: A Technical Overview
ARP operates using a simple yet powerful four-step process that is essential for network communications.
Discovering the MAC Address
When a device, known as the initiator, needs to communicate with another device within the local network but only knows the target’s IP address, it sends out an ARP request. This request is a broadcast message, asking, “Who has this IP address?”
Broadcasting Request to LAN
Since the initiator does not know the MAC address for the desired IP, the ARP request is sent to all devices on the LAN. Every device on that network segment receives the request.
Target Device Responds
Only the device with the matching IP address responds to the ARP request. This response contains the important piece of information required for communication: the device’s MAC address.
Updating ARP Cache
Once the initiator receives the MAC address from the target device, it updates its ARP cache. This cache is a table stored in the device’s memory, which reduces the need for future ARP requests between the same devices.
This efficient protocol is elemental in ensuring that computer networks operate smoothly by resolving the necessary addresses involved in data transmission. Without ARP, the dynamic and fluid exchange of information we depend on daily would be hindered.
ARP Cache: Understanding Its Significance and Management
The ARP cache plays a pivotal role in network efficiency and communication speed. Its significance stems from its function as a storage mechanism for resolved addresses, preventing the need for repetitive ARP request broadcasting. Understanding and managing the ARP cache can significantly impact your network’s performance and reliability.
Significance of the ARP Cache
The ARP cache is essential because it:
- Reduces Network Traffic: By remembering the IP-to-MAC address mappings, the ARP cache cuts down on broadcast traffic on the network.
- Speeds Up Communication: It allows for quicker data packet delivery by bypassing the need to resolve addresses for each communication attempt.
- Aids in Network Stability: A well-maintained cache prevents data from being sent to incorrect or outdated MAC addresses.
Managing the ARP Cache
Effective management of the ARP cache involves:
- Regular Inspection and Clearing: Monitor the ARP cache and clear out old or incorrect entries to maintain network integrity.
- Timely Updates: Keep the cache updated to reflect changes in the network, such as replaced or updated devices.
- Preventing Overflow: To ensure the cache does not overflow, which can cause performance issues, limit the number of entries and adjust timeouts as needed.
- Security Measures: Implement security protocols to safeguard against ARP spoofing, where a malicious actor could corrupt the ARP cache and redirect traffic.
In summary, the ARP cache aids in streamlining network communications by retaining key address information, but it requires diligent management and security considerations to uphold network performance and safety.
Security Considerations with ARP
When dealing with Address Resolution Protocol, or ARP, security is a paramount concern. This is due to ARP’s susceptibility to certain types of cyber attacks, which can lead to serious network vulnerabilities. Below are key security considerations that network administrators and users should be aware of and how to address them:
ARP Spoofing Attacks
One of the most common threats is an ARP spoofing attack. Cybercriminals can send fake ARP messages to a network. This can result in traffic being sent to an attacker’s machine instead of the correct host.
Mitigating Spoofing Risks
To prevent such attacks, a network should have robust security measures in place. Intrusion detection systems can monitor for unusual ARP traffic. Using static ARP entries where applicable can reduce risks, but this is not scalable for large networks.
Network Segmentation
Dividing a network into smaller segments can contain the impact of an ARP spoofing attack. If an attacker gains access to one segment, the others can remain secure.
Dynamic ARP Inspection
On switches that support it, dynamic ARP inspection (DAI) can be enabled. DAI checks ARP packets on the network against a trusted database. It ensures that only valid ARP responses are relayed.
Encryption and Authentication
Enhancing network security with encryption can protect the data integrity. Additionally, authentication mechanisms can verify the identity of devices on the network. This helps to prevent unauthorized access.
Proactive security measures for ARP are vital. They help maintain network integrity and protect sensitive data. Regular network audits and updates to security practices can safeguard against evolving threats.
Differences Between ARP and Other Network Protocols
When comparing ARP to other computer network protocols, several key distinctions become evident.
ARP vs. IP Protocol
ARP and IP protocols serve different functions within a network. While ARP maps IP addresses to MAC addresses, the IP protocol deals with routing packets of data between different networks. ARP operates on the local network to assist devices in communicating, whereas IP facilitates broader internet connectivity.
ARP vs. ICMP
Another comparison is between ARP and ICMP (Internet Control Message Protocol). ARP is all about address resolution, while ICMP handles error messages and operational info during network activities. ICMP tells you there’s a problem; ARP ensures devices know who they’re talking to.
ARP vs. DHCP
Dynamic Host Configuration Protocol (DHCP) assigns IP addresses to devices on the network. It’s different from ARP, which does not assign but translates known IP addresses to MAC addresses. DHCP helps devices join the network; ARP helps them communicate after joining.
ARP vs. TCP/UDP
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) concern the transport layer, managing data transmission. ARP, on the other hand, works at the link layer, dealing only with local network communication. TCP and UDP guide data packets; ARP links those packets to the right device.
ARP vs. DNS
Finally, ARP differs from DNS (Domain Name System), which translates domain names to IP addresses. ARP could be seen as closer to home, working within the local network scope, while DNS operates on a global scale, guiding web traffic across the internet.
Each protocol plays a unique role in maintaining an efficient and operational network. Understanding these differences helps network professionals ensure smooth and secure communication within and across networks.
Network Devices and ARP: Routers, Switches, and Hosts
In the landscape of computer network protocols, ARP’s role varies depending on the network device in question.
Routers and ARP
Routers leverage ARP for determining the appropriate next hop for a data packet. When a router receives a packet destined for a different network, it uses ARP to locate the MAC address of the next router within the path, often the gateway.
Switches and ARP
Switches, operating at the data link layer, utilize ARP to associate incoming data packets with the correct MAC addresses. This ensures packets are forwarded through the switch to the right destination within the local media.
Hosts and ARP
Host machines such as computers and servers depend on ARP to identify the MAC addresses of other devices within the local network. When a host wants to communicate with another local device, ARP provides the necessary translation from IP to MAC address to facilitate the data transfer.
Understanding how ARP interacts with routers, switches, and hosts enhances network efficiency and communication. It’s a critical protocol that supports the seamless integration and function of these network devices.
Best Practices for Monitoring and Managing ARP in Networks
To maintain a secure and efficient network, it is crucial to monitor and manage the Address Resolution Protocol (ARP). Here are some best practices:
Conduct Regular Network Audits
Keep track of ARP activities through ongoing network audits. This helps identify any unusual patterns that may signal security threats.
Implement Static ARP Entries
For critical network devices, consider using static ARP entries. This can prevent ARP spoofing attacks but may not be practical for all devices due to scalability issues.
Enable Dynamic ARP Inspection
On networks that support it, turn on dynamic ARP inspection. This validates ARP packets against a trusted database, ensuring authenticity and denying improper communications.
Utilize Network Security Tools
Deploy network security tools that can detect and block malicious ARP traffic. Choose software that specifically offers protection against ARP-based threats.
Educate Users
Inform users about secure practices. Awareness can prevent accidental introduction of threats to the network.
Keep Software Updated
Make sure all network devices run the latest firmware and software updates. Patches often include fixes for known vulnerabilities, including those affecting ARP.
Limit Network Access
Apply access control lists (ACLs) and segment your network. By controlling who can access certain parts of the network, you mitigate the risk of ARP spoofing within your network’s scope.
Monitor ARP Cache
Regularly check the ARP cache for any irregularities. If you find old or incorrect entries, remove them to preserve network integrity.
By following these best practices, you can enhance the ARP protocol’s efficiency and secure your network from potential threats.